Welcome to a curated list of AWS security services that are documented in a manner that a seasoned security practitioner could easily relate to. The idea here is to provide ready reckoner of the right set of AWS security tools or services that are provided natively with AWS for security teams embarking on a “security at scale” journey. AWS security services can generally be enabled at the click of a button and are billed on a pay-per-use model.
Data Security
Macie
“Data is the new gold” is a statement that has been doing the rounds for a while in the age where businesses are data driven more than ever, well it definitely is a goldmine for attackers without doubt! When one starts to think about protecting their applications or systems, it can get a little tedious to understand which system to prioritise over the other in terms of protection. Data classification is the single most important tool to help organisations automate the effort to an extent.
Macie for example, is a tool provided by AWS that scans S3 buckets and detects storage of sensitive information for example credit cards, social security numbers, personal information etc. Outputs from Macie can help to further fine tune (or prioritise) your security strategy and control implementation, for example, you would want to implement stronger controls around sensitive data compared to non-sensitive data. Another excellent example is where combination of Macie and Lambda can be leveraged to automatically protect S3 buckets and the information contained!
KMS
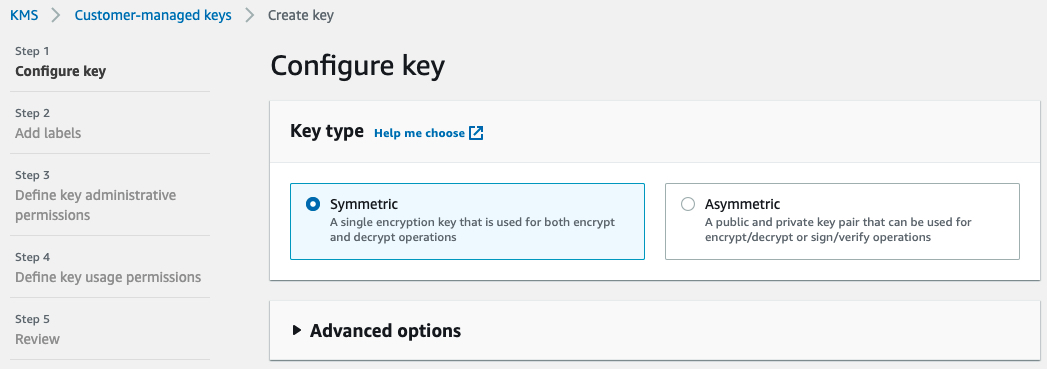
The AWS key management service enables various AWS services to encrypt data at rest. Services such as S3, EBS, Redshift, OpenSearch etc, can encrypt their data stores using customer defined keys in AWS KMS. KMS is highly recommended in services that store or process sensitive information. AWS customers can create a KMS key in a few clicks and then apply the keys in relevant resource configurations as shown below. Central controls such as key strength, rotation can be managed as here as well.
KMS Key Creation:
Applying the KMS Key in an S3 Bucket:
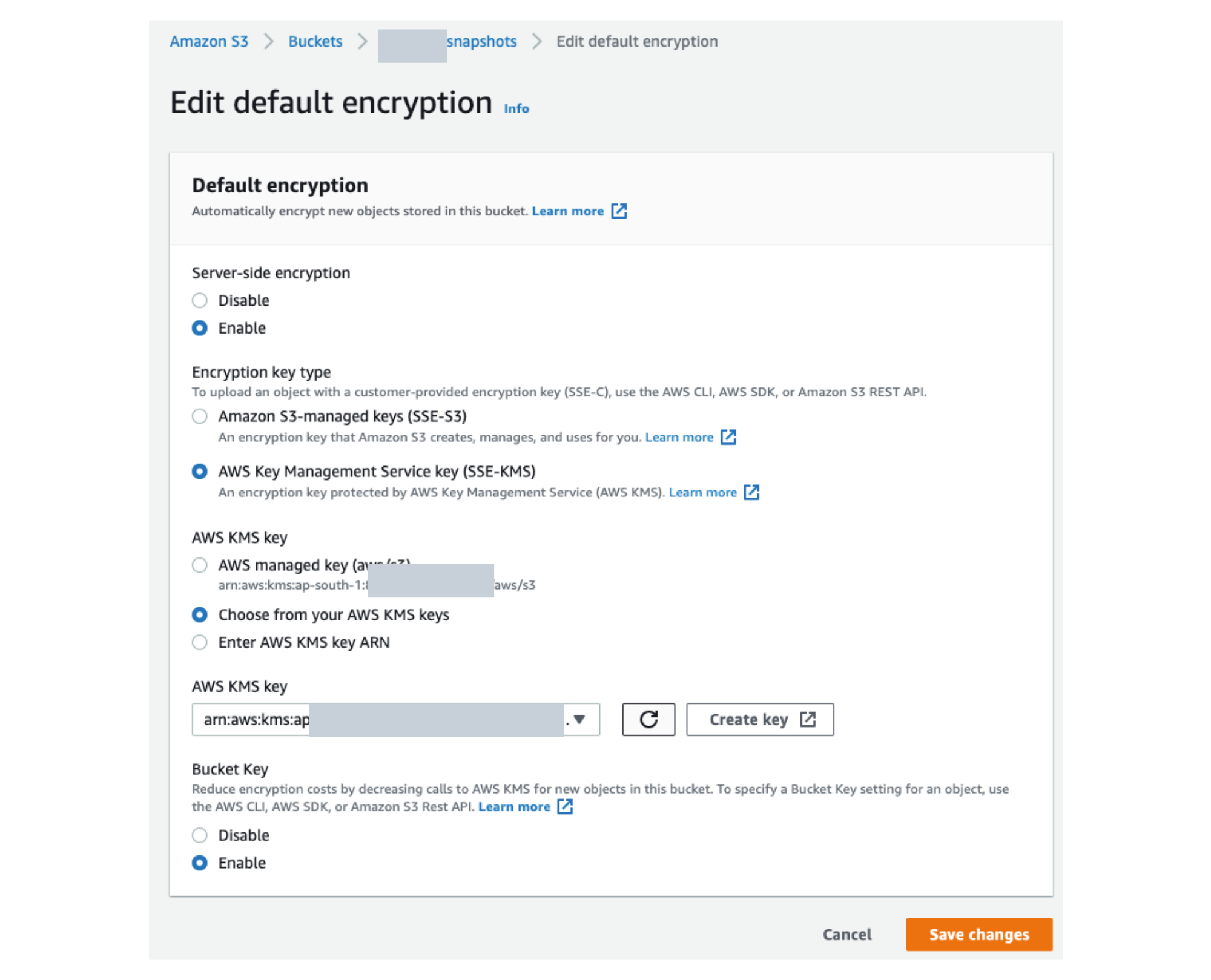
Pro tip : one can use Macie to first classify resources and then use KMS to encrypt sensitive ones.
Cloud HSM
Organisations that store or process highly sensitive information such as credit card numbers (or similar), can leverage the cloud hardware security module to store such information using industry grade encryption techniques. The Cloud HSM service creates a cluster that can be logically separated on the network using subnets. Below is a snippet of how easy it is to create a Cloud HSM Cluster.
Infrastructure Security
Inspector
Scans AWS infrastructure for vulnerabilities similar to a host based VA scanning tool and generates reports. AWS Inspector integrates well with complementing services such as security hub to provide a customer with a single pane of glass with respect to their security posture. One of the best things about Inspector unlike traditional vulnerability scanning tools is, that it requires minimal configuration and zero infrastructure investments.
Secrets Manager
Credentials (or secrets) are your keys to the kingdom. To add to that, with public cloud relying lesser and lesser on network boundaries, accidental disclosure of secrets in public code repositories or client side code can be catastrophic to businesses. The AWS Secrets Manager service is a secure store for managing credentials at scale. It provides a host of features such as secret rotation, encryption, fine grained access control.
Pro tip : secrets manager is priced according to the number secrets stored as well as the number of calls made from an application to retrieve the secret. It is highly recommended to cache secrets in application memory in case you’re expecting a huge number of calls to the secrets manager service.
Systems Manager
AWS systems manager is more of an infrastructure management tool, but very useful for security as well by automating patch management, security configuration reviews and compliance management. Organisations can write custom hooks from inspector that would trigger an upgrade job on systems manager in case a vulnerability is found due to older system or sub-system versions.
Session Manager
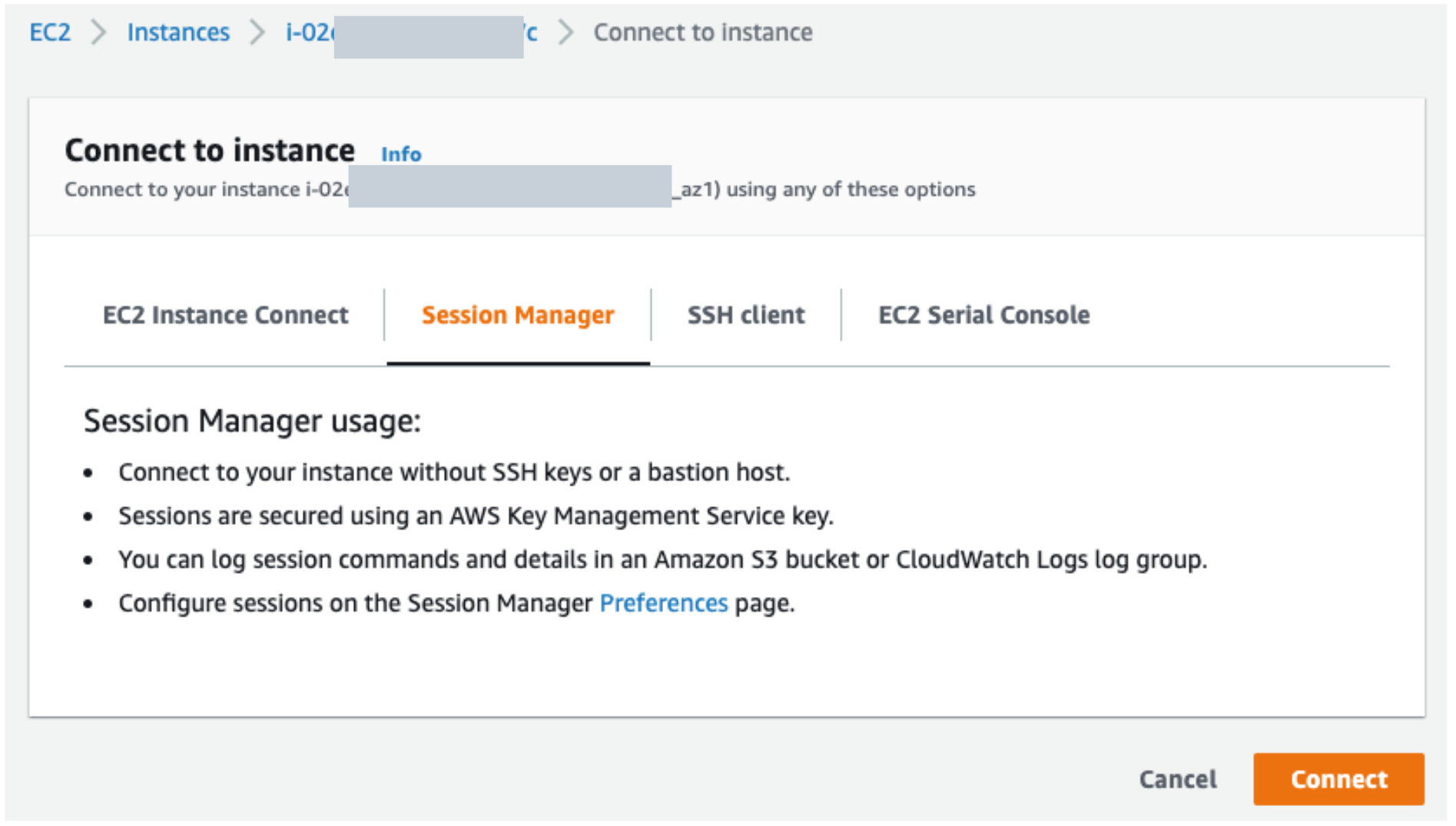
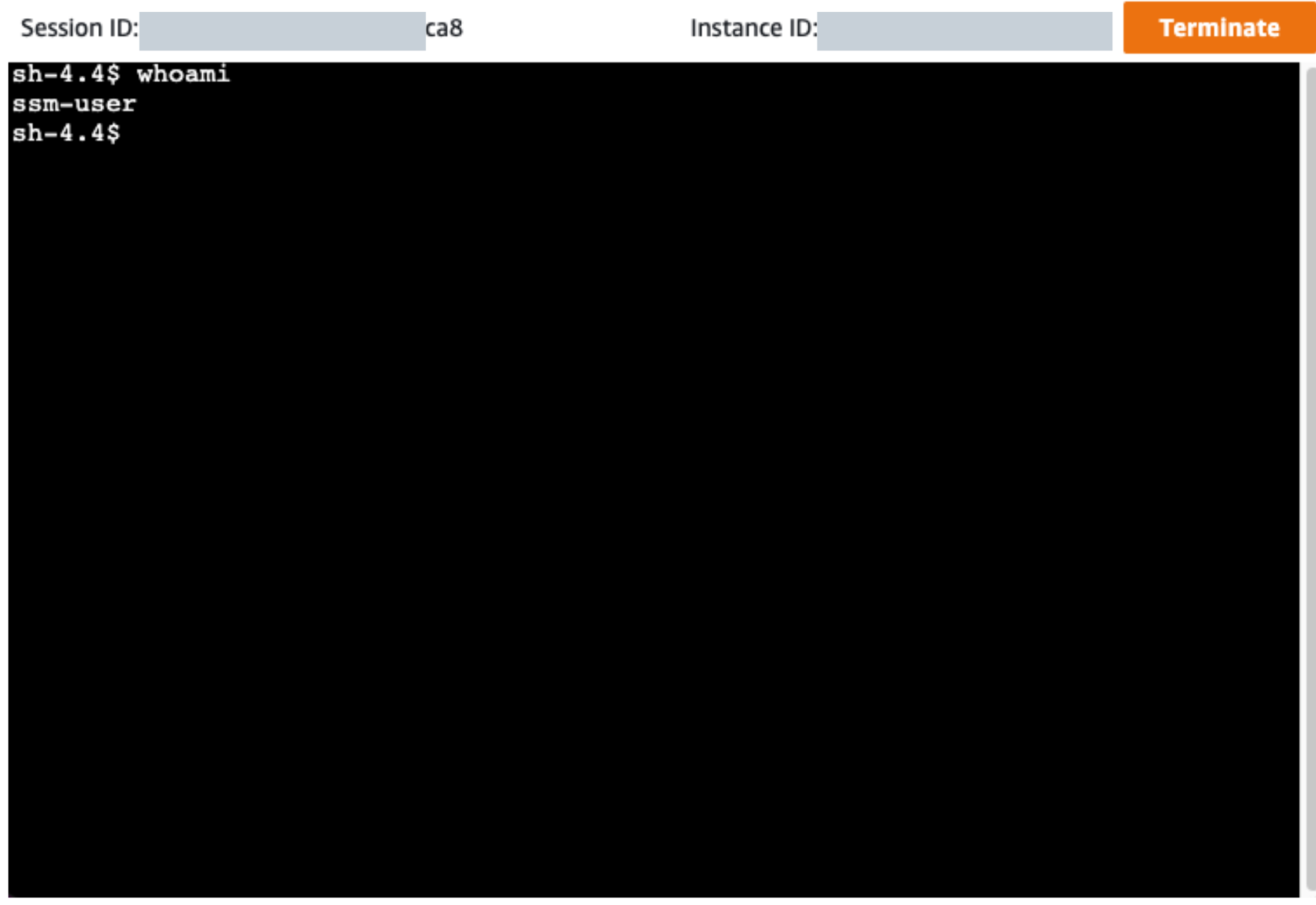
A very useful tool shipped with Systems Manager! Session manager provides infrastructure teams with browser based terminal access to instances, hence eliminating the need to open sensitive ports and also logging every command to a destination of choice such as S3, CloudWatch etc. Using session manager requires an SSM IAM role to be applied to EC2 instances and internet connectivity such that the browser based terminal can be enabled.
Connecting with session manager to a virtual machine:
Sample terminal:
Threat Detection & Response
No preventive security strategy is ever enough, the bad guys mange to find ways into networks and applications, it’s just a matter of time. Let’s look at some important AWS tools that help catching such intrusion attempts early on in it’s game.
GuardDuty
AWS GuardDuty is a managed threat detection service that analyses VPC flow logs, DNS logs and CloudTrail events to detect threats lurking around in an AWS environment. It baselines user, resource and API activity to then detect deviations in normal behaviour; which acts as an early warning signal to compromise or infiltration. GuardDuty also contains threat intelligence feeds from renowned sources such as ProofPoint and CrowdStrike to flag communication to known malicious internet IP addresses. Alerts are classified basis severity, and can be integrated into security hub as well.
CloudTrail
Probably the most important AWS service from a security point of view. CloudTrail logs all interactions (whether user or API) with AWS and stores events in an S3 bucket for analysis. These events are extremely important for analysis or investigation purposes in the event of a breach, or routine reviews. There are two ways to analyse CloudTrail logs:
- CloudWatch – CloudTrail logs can be sent to CloudWatch for storage and analysis. Further, CloudWatch alarms can be created for sensitive AWS activity such as S3 buckets made public, or security groups opened up from 0.0.0.0/0 (or the internet)
- Athena – One could create an Athena view over the S3 bucket to ease out CloudTrail analysis.
Lambda Functions
AWS services are extremely flexible and can be connected to each other via triggers. Lambda functions, for instance can be used to automate routine tasks or incident response procedures such as containing an EC2 instance post a compromise or reverting a permissive IAM (or security group) change. They can be integrated with GuardDuty, Security Hub or CloudWatch to perform actions basis certain conditions, hence reducing the overhead on security teams.
Pro Tip : use lambda functions for the obvious kind of actions to begin with, such as reverting a security group opened up from 0.0.0.0/0; this can be done by triggering an action when an event called “AuthorizeSecurityGroupIngress” is called and logged by CloudTrail.ser
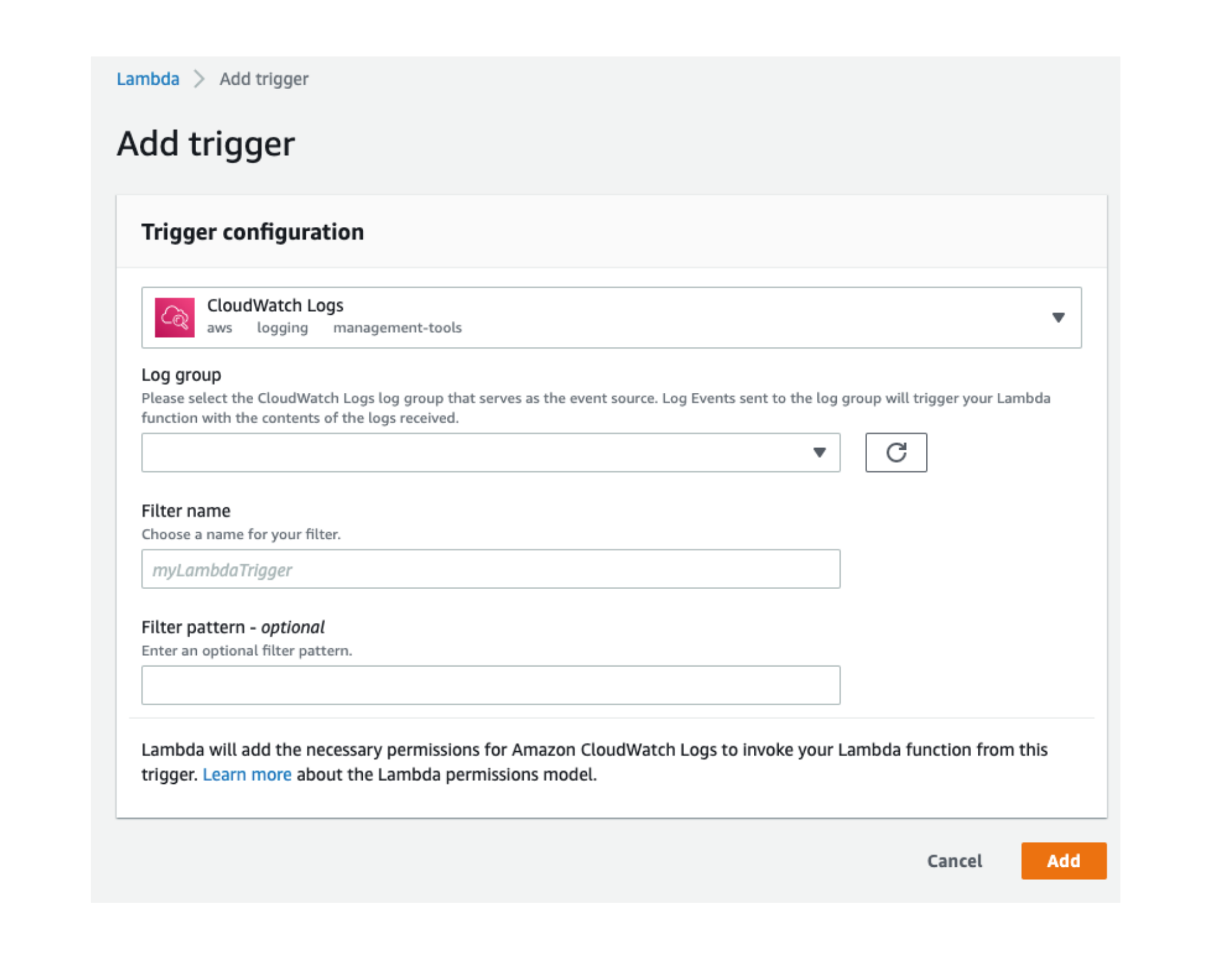
Adding a Lambda trigger from CloudWatch: