Draft DPDP Rules 2025 – The Real Deal

Deep dive into the DPDP Rules announced in January 2025, which are likely to get enforced this year.
21 Cloud Security Tools for Hyper Growth Companies

What is Cloud Security? Cloud computing is a hosted service offered as software, hardware, or even storage over the web, often as a vital part of multi or hybrid cloud infrastructure. It provides excellent benefits such as faster deployments, scalability, agility, flexibility, and reduced up-front costs, regardless of the business size. By the same token, […]
Security Services in a Nutshell at re:Invent 2022

Public cloud is by far the most talked about topic in the infrastructure space today. According to Gartner, public cloud adoption has grown at an unprecedented rate over the last, and 20.4% in 2022 alone. During COVID, businesses that were offline, have gone online with the intent to stay relevant and public cloud happens to […]
16 AWS IAM Best Practices You Should Know

Before we get started with best practices around using AWS IAM, let’s get our head around some underlying concepts and risks associated with “not getting IAM right”. Though this post uses AWS IAM as a reference point, readers & security practitioners can draw a parallel to other public cloud IAM implementations as well. AWS Authentication […]
AWS Security Group Best Practices

What is a Security Group? An AWS security group is a virtual firewall which can be applied to one or more AWS resources to control its inbound traffic. One thing to keep in mind is that AWS security groups are all permissive in nature which means you can’t deny specific traffic sources with this firewall, you can […]
A Practical Approach to CERT-In 70B Compliance

CERT (Computer Emergency Response Team) India is a national nodal agency that’s been around since 2004 and responsible for responding to cyber security incidents as they occur. India has faced an increasing level of cyber attacks over the last few years. In fact, according to an article by Business Standard, India is among the top 3 […]
Practical AWS Logging in 5 Steps
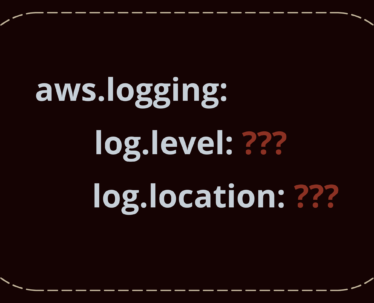
Logging is probably one of the most crucial areas when a security or operational incident needs to be investigated…. is what most technology practitioners would say. But, monitoring logs for malicious or unusual activity, carrying out threat hunting are proactive techniques to help organisations catch infiltrations or compromise early. This is KEY to reducing the […]
14 AWS S3 Security Best Practices
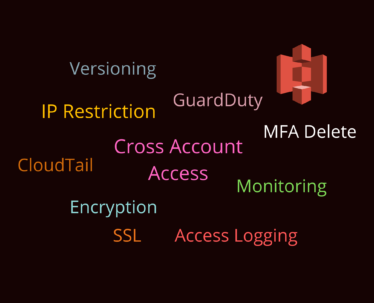
S3 or Simple Storage Service : the most popular service in AWS and undoubtedly the most low hanging service from a security misconfiguration perspective. Over the years, organisations hosted on public cloud have seen a series of breaches arising due to misconfigured S3 buckets or lack of S3 security controls. Organisations such as WWE, Dow […]
Denonia – Guide to Prevention & Detection

Well it’s not unheard of, that security issues, malware or exploits often follow soon after an emerging technology finds prominence. Denonia, the first Lambda malware is out. Originally discovered by Cado Labs a few days ago, Denonia specifically targets Lambda functions with the intent to deploy code that carries out bitcoin mining, hence significantly increasing AWS costs […]
17 Open Source Cloud Security Tools You Should Explore

Cloud adoption is growing, at an ACCELERATED rate! The bad guys love the cloud too, since it’s where valuable data resides, and is often prone to misconfigurations or errors if it’s not dealt with properly. We’ll talk about 17 open source cloud security tools that have helped organizations globally over the years. Here goes! Cloud […]