Did you know that 94% of enterprises already use cloud services, yet 65% of cloud security incidents are caused by misconfigurations? In today’s digital landscape, organizations are rapidly adopting cloud computing to drive innovation, scalability, and cost-efficiency. However, as cloud adoption grows, so do the challenges of ensuring data security and privacy. Imagine this: a single misconfigured setting could expose sensitive customer data or bring your operations to a halt.
Enter Cloud Security Posture Management (CSPM), a proactive approach to identifying, mitigating, and managing vulnerabilities in cloud environments. Think of CSPM as your cloud’s immune system—constantly monitoring, detecting, and neutralizing threats before they cause harm.
In this blog, we’ll dive deep into what CSPM is, why it’s a game-changer, its key components, best practices, and how it can help organizations secure their cloud infrastructure.
Whether you’re a startup or a NSE listed company, CSPM is no longer optional—it’s essential for staying ahead in the ever-evolving world of cloud computing. Ready to take control of your cloud security? Let’s get started!
What is Cloud Security Posture Management (CSPM)?
Imagine this: a major e-commerce company accidentally leaves a cloud storage bucket publicly accessible, exposing millions of customer records. Or a healthcare provider misconfigures its cloud database, violating HIPAA compliance and facing hefty fines. These aren’t just hypothetical scenarios—they’re real-world incidents that happen more often than you’d think. Cloud Security Posture Management (CSPM) is the safety net that prevents such disasters. It’s a methodology and set of tools designed to continuously monitor cloud environments for compliance and security risks. Think of CSPM as your cloud’s watchdog, always on the lookout for misconfigurations, unauthorized access, or policy violations.
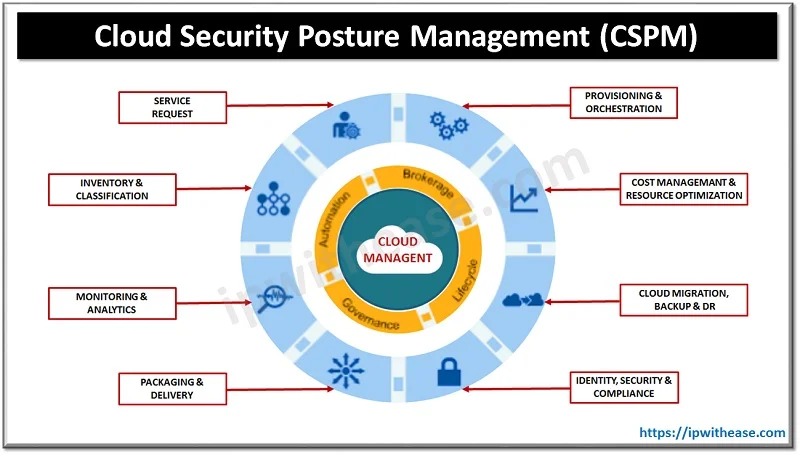
The primary goal of CSPM is to ensure that an organization’s cloud infrastructure aligns with security policies, regulatory standards, and best practices. By providing real-time visibility into cloud configurations, CSPM helps organizations detect misconfigurations, enforce security policies, and maintain compliance. For example, a financial institution using CSPM can automatically detect and fix an open S3 bucket before it becomes a headline-making data breach.
According to Gartner, the CSPM market is booming, with revenue forecasted to grow from 1.34 billion in 2023 to 3.32 billion in 2027, at a 25.7% CAGR. This growth is driven by the increasing adoption of public cloud, private cloud, containers, and serverless computing. By 2027, 80% of vendors are expected to offer CSPM as a core feature of their cloud security platforms.
But why is CSPM gaining so much traction? Consider this: a global retail chain using CSPM tools identified and resolved over 500 misconfigurations in a single quarter, saving millions in potential fines and reputational damage. Or a tech startup that leveraged CSPM to achieve GDPR compliance in just weeks, avoiding costly delays. These examples highlight how CSPM isn’t just a tool—it’s a strategic advantage in today’s cloud-first world.
Whether you’re a small business or a multinational corporation, CSPM ensures your cloud environment is secure, compliant, and optimized.
Why is CSPM Important?
CSPM isn’t just a tool—it’s a strategic advantage in today’s cloud-first world. CSPM ensures your cloud environment is secure, compliant, and optimized.

Preventing Data Breaches
Misconfigurations are the leading cause of cloud data breaches, often resulting from human error or oversight. For instance, a single misconfigured S3 bucket can expose sensitive customer data to the public internet, leading to devastating consequences. CSPM tools act as your first line of defense by identifying incorrect settings—like open ports or overly permissive access controls—and automating corrective actions. Imagine a scenario where your team accidentally leaves a database unprotected. With CSPM, the tool would detect this in real-time, lock it down, and notify your team, significantly reducing the risk of a breach.
Actionable Tips
- Regularly audit your cloud configurations using CSPM tools.
- Enable automated remediation to fix misconfigurations instantly.
- Train your team on common misconfiguration risks and best practices.
Ensuring Compliance
Regulatory requirements like GDPR, HIPAA, and PCI DSS are not only complex but also constantly evolving. Staying compliant can feel like navigating a maze. CSPM tools simplify this process by providing a comprehensive view of your organization’s compliance status. For example, if your cloud environment doesn’t meet GDPR’s data residency requirements, CSPM will flag the issue and guide your team on how to resolve it. This ensures you avoid hefty fines and reputational damage.
Actionable Tips
- Use CSPM to generate compliance reports for audits.
- Set up alerts for policy violations to address them immediately.
- Regularly update your CSPM policies to align with the latest regulations.
Optimizing Resources
Did you know that 30% of cloud spending is wasted on unused or underutilized resources? CSPM continuously monitors your cloud environment, identifying idle virtual machines, unattached storage volumes, or over-provisioned instances. By optimizing these resources, you not only reduce costs but also minimize your attack surface. For instance, a company using CSPM discovered $50,000 in annual savings by shutting down unused resources.
Actionable Tips
- Schedule regular reviews of your cloud resource usage.
- Automate resource cleanup with CSPM tools.
- Use cost optimization dashboards to track savings.
Proactive Risk Management
Instead of waiting for vulnerabilities to cause damage, CSPM proactively identifies and addresses risks. For example, if a new vulnerability is discovered in your cloud environment, CSPM tools can detect it, assess its severity, and either patch it automatically or alert your team for immediate action. This reduces downtime, enhances business continuity, and keeps your operations running smoothly.
Actionable Tips
- Enable real-time threat detection and alerts.
- Prioritize high-severity risks for immediate action.
- Conduct regular risk assessments using CSPM insights.

Key Components of CSPM
Continuous Monitoring
CSPM tools offer 24/7 surveillance of cloud resources, configurations, and data access. This helps detect anomalies, misconfigurations, and vulnerabilities in real-time. For example, if an employee accidentally grants public access to a sensitive database, CSPM will flag it instantly.
Automated Remediation
CSPM can automate corrective actions to address detected issues quickly. Imagine a scenario where a misconfigured firewall rule is automatically fixed before it can be exploited.
Policy Enforcement
Security policies are crucial for maintaining compliance. CSPM ensures that cloud resources adhere to these policies, promptly alerting administrators when non-compliance occurs.
Compliance Management
CSPM tools provide a comprehensive view of your compliance status, helping you meet standards like GDPR, HIPAA, and PCI DSS.
Risk Assessment
By identifying and categorizing risks according to severity, CSPM helps prioritize response efforts. For instance, a critical vulnerability in your authentication system would be flagged as high priority.
Best Practices for Effective CSPM
Integration Across Platforms
In today’s multi-cloud and hybrid environments, security gaps can easily arise when tools don’t communicate effectively. A robust CSPM solution integrates seamlessly across platforms like AWS, Azure, and Google Cloud, providing a unified view of your security posture. For example, a company using multiple cloud providers can leverage CSPM to monitor all environments from a single dashboard, ensuring no vulnerabilities slip through the cracks.
- Gain a 360-degree view of your cloud security across all platforms.
- Reduce complexity by managing multi-cloud environments from one interface.
- Ensure consistent policy enforcement, no matter which cloud provider you use.
Baseline Configuration Policies
Establishing baseline configuration policies is like setting the “gold standard” for your cloud environment. These policies act as a benchmark, allowing CSPM tools to compare real-time data and swiftly detect deviations. For instance, if your baseline policy requires all databases to be encrypted, CSPM will flag any unencrypted databases immediately.
- Create a proactive defense mechanism by identifying deviations before they become risks.
- Simplify compliance audits with predefined, standardized configurations.
- Reduce manual effort by automating policy enforcement.
Automate When Possible
Automation is the backbone of effective cloud security. By automating remediation processes, you minimize human error and drastically reduce the mean time to detect and respond (MTTD/MTTR) to incidents. Imagine a scenario where a misconfigured firewall rule is automatically fixed within seconds, preventing a potential breach.
- Save time and resources by automating repetitive tasks.
- Improve response times, reducing the window of exposure to threats.
- Free up your team to focus on strategic initiatives rather than manual fixes.
Regular Security Training
Even the best tools can’t compensate for human error. Regular security training ensures your team understands best practices and the importance of compliance. For example, a well-trained employee is less likely to accidentally expose sensitive data or ignore a critical alert.
- Build a security-first culture within your organization.
- Reduce accidental vulnerabilities caused by human error.
- Empower your team to act as the first line of defense.
Continuous Improvement
Cloud threats are constantly evolving, and so should your security strategy. Regularly updating your CSPM policies and processes ensures you stay ahead of emerging risks. For instance, if a new type of ransomware targets cloud environments, your CSPM solution can be updated to detect and block it.
- Stay future-proof by adapting to new threats and technologies.
- Continuously optimize your security posture based on real-world insights.
- Ensure your CSPM solution evolves alongside your business needs.
Implementing these best practices isn’t just about securing your cloud—it’s about future-proofing your business. By integrating across platforms, establishing baselines, automating processes, training your team, and continuously improving, you create a robust security framework that adapts to your needs.
Actionable Tips
- Start with a CSPM assessment to identify gaps in your current strategy.
- Schedule quarterly reviews to update policies and train your team.
- Leverage automation to streamline security operations and reduce risks.

Selecting the Right CSPM Solution
Choosing the right Cloud Security Posture Management (CSPM) solution is like picking the perfect security guard for your cloud environment—it needs to understand your unique needs, adapt to your growth, and respond swiftly to threats. To make the best decision, start with a clear understanding of your organization’s cloud architecture, compliance requirements, and security goals. Here’s what to look for-
1. Compatibility
Your CSPM solution should seamlessly integrate with your existing cloud platforms and services, whether you’re using AWS, Azure, Google Cloud, or a multi-cloud setup. For example, if your business relies heavily on AWS for hosting and Azure for data analytics, your CSPM tool should provide equal visibility and control across both platforms.
- Avoid vendor lock-in by choosing a solution that works across multiple clouds.
- Ensure consistent security policies and monitoring across all environments.
- Simplify management by consolidating tools into one platform.
2. Scalability
As your business grows, so does your cloud infrastructure. A scalable CSPM solution grows with you, ensuring performance isn’t compromised. Imagine your company doubles its cloud usage overnight—your CSPM tool should handle the increased workload without missing a beat.
- Future-proof your investment by choosing a solution that scales with your needs.
- Maintain high performance even during rapid growth or peak usage.
- Reduce the need for frequent tool upgrades or replacements.
3. Customization
No two organizations are alike, and neither are their security needs. A good CSPM solution allows you to customize policies, alerts, and workflows to fit your unique requirements. For instance, a healthcare provider might need stricter access controls compared to a retail business.
- Tailor security policies to match your industry and compliance needs.
- Set up custom alerts for specific risks or thresholds.
- Adapt the tool to your team’s workflows for smoother operations.
4. Reporting
Robust reporting capabilities are essential for demonstrating compliance and communicating risks to stakeholders. A CSPM solution with detailed, customizable reports can save hours during audits and help you make data-driven decisions.
- Simplify compliance audits with pre-built report templates.
- Provide stakeholders with clear, actionable insights into your security posture.
- Track progress over time with historical data and trend analysis.
5. Vendor Support
Even the best tools can’t replace the value of reliable vendor support. Ensure your CSPM provider offers timely assistance, comprehensive documentation, and resources like training or webinars. For example, if you encounter a critical issue at 2 a.m., you’ll want a support team that’s just a call away.
- Minimize downtime with fast, reliable support.
- Access training resources to maximize your team’s efficiency.
- Stay updated on new features and best practices through vendor-provided content.
Selecting the right CSPM solution isn’t just about features—it’s about finding a partner that aligns with your business goals and grows with you. By focusing on compatibility, scalability, customization, reporting, and vendor support, you can build a cloud security strategy that’s both robust and adaptable.

How can Cy5 Help You Achieve Continuous Cloud Monitoring and Compliance?
Cy5 is a SaaS-based cloud security posture management platform designed to help organizations continuously monitor their cloud environments for security risks and misconfigurations. But Cy5 isn’t just another tool—it’s your strategic partner in building a secure, compliant, and optimized cloud infrastructure.
Cy5 goes beyond basic monitoring by providing contextual intelligence about your cloud environment. This means it doesn’t just flag risks—it explains why they matter and how they impact your business. For example, if a misconfigured database is detected, Cy5 will show you its exposure level, potential impact, and recommended actions. This level of insight helps you make informed decisions and prioritize risks that truly matter, reducing noise and focusing on what’s critical.
Not all alerts are created equal, and Cy5 understands this. It prioritizes alerts based on their severity and risk, ensuring your team focuses on the most critical issues first. Imagine receiving hundreds of alerts daily—Cy5 helps you cut through the clutter and address high-priority threats immediately. This not only saves time but also reduces alert fatigue, allowing your security team to operate more efficiently and effectively.
Staying compliant with standards like PCI DSS, HIPAA, and GDPR can feel overwhelming, but Cy5 simplifies this process. It provides a comprehensive compliance dashboard that tracks your adherence to industry standards in real-time. For instance, if a new GDPR requirement is introduced, Cy5 will guide you through the necessary changes to stay compliant. This proactive approach helps you avoid fines, reputational damage, and the stress of last-minute audits.
Check Out More: Cy5 | Actionable Security Signals, at Cloud Speed
Beyond its advanced features, Cy5 offers expert services and security solution to help you maximize your cloud security. From onboarding support to custom policy creation, Cy5’s team of experts ensures you get the most out of the platform. For example, if you’re migrating to a multi-cloud setup, Cy5 can help you design a security strategy tailored to your needs. This hands-on support ensures your cloud environment is not only secure but also optimized for performance and compliance.
“Cy5 isn’t just a platform—it’s a partner in your cloud security journey.” With its advanced features, expert services, and commitment to innovation, Cy5 empowers you to stay ahead of threats, maintain compliance, and optimize your cloud environment. Ready to transform your cloud security?
Final Thoughts
Cloud Security Posture Management (CSPM) has transitioned from a luxury to a mission-critical necessity for organizations aiming to protect their cloud environments from ever-evolving threats. With features like continuous monitoring, automated remediation, and compliance management, CSPM tools empower businesses to build a resilient security framework while optimizing resources and meeting regulatory demands.
By investing in a robust CSPM solution and embracing best practices, organizations can proactively address risks, ensuring uninterrupted operations and peace of mind. The future of cloud security is here—don’t just adapt, lead the way.
FAQs (Cloud Security Posture Management): Answers to Your Top CSPM Questions | Cy5
How Does CSPM Ensure Continuous Cloud Security & Visibility?
CSPM provides continuous security monitoring by:
- Discovering Cloud Assets – Scanning compute, storage, networking, and serverless resources for real-time inventory.
- Analyzing Security Posture – Identifying misconfigurations and risky configurations.
- Compliance & Governance – Ensuring cloud deployments follow security frameworks like CIS, GDPR, or ISO 27001.
- Automating Remediation – Some CSPM tools can auto-fix misconfigurations, such as restricting open ports or enforcing encryption.
By integrating CSPM into DevSecOps, organizations get proactive security without slowing down cloud operations.
What Are Some Common CSPM Security Checks?
CSPM tools help detect misconfigurations and security risks in cloud environments. Some key checks include:
➤ S3 Bucket Misconfigurations – Identifies publicly accessible storage buckets.
➤ IAM Policy Risks – Detects overly permissive user roles or leaked credentials.
➤ Misconfigured Security Groups – Flags open SSH/RDP ports that expose cloud servers.
➤ Unencrypted Data – Ensures sensitive information is protected at rest and in transit.
➤ Exposed API Endpoints – Alerts on unauthenticated API access, reducing attack vectors.
Why do Cloud Data Breaches Occur? How does CSPM Help Prevent Them?
Cloud data breaches happen primarily due to misconfigurations, weak access controls, and exposed sensitive data. Common causes include:
- Overly permissive IAM policies (unrestricted user access)
- Publicly exposed S3 buckets or storage
- Unsecured API endpoints
- Use of hardcoded or leaked credentials
How will CSPM Help?
◆ Automated Misconfiguration Detection – Identifies weak security settings across compute, storage, and network resources.
◆ Continuous Compliance Checks – Ensures cloud environments meet security best practices (e.g., PCI-DSS, NIST, SOC 2).
◆ Alerting & Monitoring – Flags high-risk changes in real-time so teams can act before an attacker exploits them.
Pro Tip: Combine CSPM with threat detection tools like Cloud SIEM to catch attacks that bypass preventive controls.
Why do Cloud Misconfigurations Happen?
Misconfigurations are the #1 cause of cloud security failures. They occur due to:
- Complexity – Public cloud providers (AWS, Azure, GCP) offer hundreds of services, making secure setup challenging.
- Lack of Cloud Security Knowledge – Many IT and DevOps teams are not security experts, leading to missteps like overly broad IAM roles.
- Speed vs. Security Trade-offs – Teams often prioritize deployment speed over security, leaving assets exposed.
- Human Error – Simple mistakes, like making a storage bucket public instead of private, can lead to data leaks.
Solution:
Using CSPM tools helps teams automate security checks, detect risky settings, and enforce security policies before issues escalate.
How does Data Security Posture Management (DSPM) Complement CSPM?
While CSPM secures cloud infrastructure, DSPM focuses on data protection. They work together to:
- Identify Sensitive Data – DSPM classifies PII, financial records, and critical business data.
- Prevent Data Leaks – CSPM fixes misconfigurations, while DSPM ensures data-level security policies are enforced.
- Access & Permissions Management – CSPM secures IAM roles, DSPM monitors how data is accessed and used.
For complete cloud security, businesses should combine CSPM and DSPM with SIEM or XDR solutions.
What are the Key Use Cases of CSPM?
Organizations use CSPM for:
- Security Posture Monitoring – Detecting vulnerabilities and weak configurations.
- Compliance Automation – Ensuring adherence to frameworks like SOC 2, PCI-DSS, and HIPAA.
- Threat Detection & Remediation – Identifying risky changes and automating fixes before they become breaches.
- Multi-Cloud Security – Managing security across AWS, Azure, and Google Cloud from a single dashboard.
- DevSecOps Integration – Catching misconfigurations before deployment using infrastructure-as-code (IaC) scanning.
Why is CSPM Critical for Businesses?
CSPM is essential because:
- 80% of cloud breaches occur due to misconfigurations (IDC Report).
- Automates compliance checks to meet regulatory standards.
- Reduces security risks by detecting threats early.
- Improves cloud visibility across multi-cloud environments.
- Minimizes manual security workload, allowing teams to focus on innovation.
For enterprises, CSPM is not optional—it’s a necessity for maintaining a secure cloud environment.
How Does CSPM Help in Continuous Cloud Security Management?
CSPM ensures continuous protection by:
- Regularly scanning cloud environments for security misconfigurations.
- Providing real-time alerts when a risk is detected.
- Automating compliance reporting for easier audits.
- Supporting proactive security by integrating with DevOps pipelines.
With CSPM, security teams can keep up with fast-changing cloud environments without increasing operational burdens.
What Is Cloud Security Posture Assessment?
A Cloud Security Posture Assessment is an evaluation of an organization’s cloud security posture to:
- Identify security gaps and misconfigurations.
- Assess compliance adherence to standards like CIS, NIST, or GDPR.
- Prioritize risk remediation based on severity.
Difference Between CSPM & Cloud Security Posture Assessment
- Cloud Security Posture Assessment is a one-time review of security gaps.
- CSPM provides continuous security monitoring with automated remediation.
Businesses should perform regular assessments and implement CSPM for long-term cloud security.
What are the Limitations of CSPM?
Cloud Security Posture Management (CSPM) is highly effective for visibility, misconfiguration detection, and compliance in cloud environments. However, it has a few limitations:
- No Runtime Protection – CSPM focuses on preventive security but does not actively block or stop real-time attacks.
- Limited Context Awareness – While CSPM detects security gaps, it may not always differentiate between critical and non-critical risks without additional tools.
- Manual Remediation Required – While some CSPM solutions offer automated fixes, complex security issues often require manual intervention.
- Integration Challenges – CSPM tools need to be fine-tuned to work smoothly with existing DevOps, security tools, and multi-cloud deployments.
Solution
To overcome these limitations, organizations can complement CSPM with Cloud SIEM, CIEM (Cloud Infrastructure Entitlement Management), and DSPM (Data Security Posture Management) for end-to-end security coverage.