Here’s something most security vendors won’t tell you: cloud-native architecture broke security. Not in a dramatic, catastrophic way, but in a thousand small cuts that add up to serious problems.
Think about it. 10 years ago, securing an application was relatively straightforward. You had a perimeter, some firewalls, maybe a WAF if you were fancy. Applications lived on servers you could actually see and touch (or at least SSH into without going through twelve authentication layers). Security teams knew where everything was, what it did, and who could access it.
Then containers happened. Then Kubernetes. Then serverless. Then someone in your engineering team decided to split your monolith into 47 microservices, each with its own database, API, and apparently, its own definition of “secure enough.”
Now? Now you’ve got containers that live for three minutes. Serverless functions that execute 10,000 times a day but only exist during execution. Kubernetes clusters where pods are constantly being born and dying like digital mayflies. And somehow, you’re supposed to secure all of this with the same tools you used to protect those nice, stable virtual machines.
It doesn’t work. And the industry knows it doesn’t work.
That’s where Cloud-Native Application Protection Platforms – mercifully shortened to CNAPP—come in. CNAPP isn’t just rebranding old tools. It’s actually trying to solve a real problem: you can’t secure cloud-native applications with a dozen disconnected security tools that don’t talk to each other.
Here’s the uncomfortable truth that drove CNAPP’s creation: almost half of organizations regularly push code with known vulnerabilities to production. Not occasionally. Regularly. And 97% experienced a cybersecurity incident related to their own applications in the previous year. These aren’t small companies with immature security practices. These are enterprises with security teams, compliance requirements, and expensive security tools.
So what went wrong?
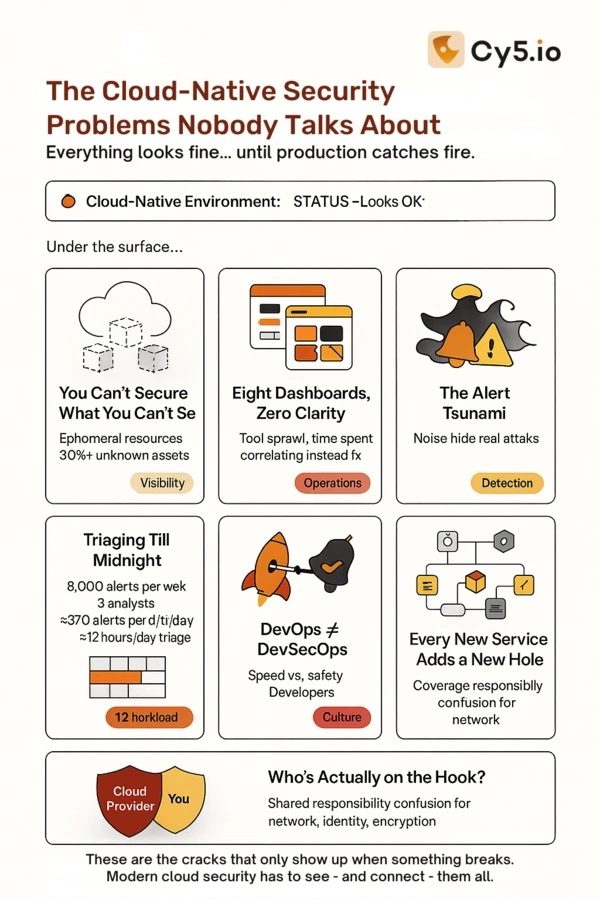
The problem isn’t that security teams are incompetent or that developers don’t care. The problem is that cloud-native environments generate so much security noise that finding actual threats becomes nearly impossible. When you’re getting 10,000 alerts a day from eight different security tools, all screaming about different issues in different languages with different severity scales, what are you supposed to do? You do what every overwhelmed human does: you prioritize badly, miss the important stuff, and hope nothing blows up.
Gartner coined the term CNAPP back in 2021, and it’s been evolving rapidly ever since. At its core, CNAPP consolidates multiple security capabilities—cloud security posture management, workload protection, identity and access management, Infrastructure as Code scanning, Kubernetes security, data security, and threat detection—into one unified platform.
When Your Security Tools Stop Making Sense
Ask most security leaders about their current toolstack, and you’ll hear some version of the same story: “We’re drowning.”
Your organization probably uses separate platforms for checking cloud configurations, scanning containers, managing who has access to what, scanning infrastructure templates, and handling actual threats. Each tool sends alerts to different dashboards. Each has its own learning curve. And most importantly—they don’t talk to each other.
Last quarter, your team might have caught a critical misconfiguration in an S3 bucket, flagged a vulnerable container image, and identified excessive permissions on a service account. But here’s the thing: none of your tools correlated these issues. Separately, each finding looked manageable. Together? They created an exploitable attack path your security team almost missed.
This fragmentation isn’t a minor inconvenience—it’s a fundamental weakness in how organizations protect cloud infrastructure. When your security information lives in silos, you’re essentially flying blind while pretending you have radar.
This is where the conversation about unified platforms becomes unavoidable.
Just in Case if You Need: How to Find and Fix Public S3 Buckets in AWS: 10-Minute Security Audit
Understanding Cloud-Native First (And Why Security Failed to Keep Up)
What Cloud-Native Actually Changed
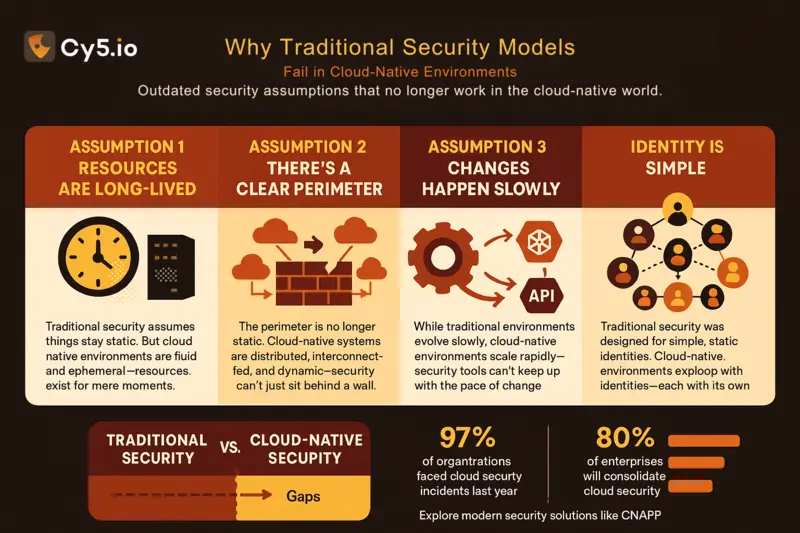
Traditional application infrastructure was built for predictability. You’d spin up a VM, it would run for months or years, and you’d protect it the same way you protected any server—firewalls at the edges, agents on the machines, periodic updates.
Cloud-native architectures flipped this model. Instead of long-lived VMs, you have containers that start and stop within seconds. Instead of static configurations, you have infrastructure defined in code and changing constantly. Instead of everything being within your organization’s network, you have services distributed across multiple clouds, regions, and third-party providers.
The technologies enabling this shift – containers, Kubernetes, serverless functions, microservices – all solve real business problems. They let your teams move faster, scale more efficiently, and build systems that adapt to demand. They’re genuinely transformative.
But they also created security challenges that existing tools weren’t designed to handle.
Why Legacy Security Approaches Fail
The traditional security model depended on knowing what you had and where it was. Your infrastructure was relatively stable. Your applications had clear boundaries. Your network perimeter was something you could actually defend.
Cloud-native obliterates these assumptions:
Ephemeral resources vanish in minutes. A container that exists for 90 seconds doesn’t give you time to deploy an agent, scan it, and report findings. By the time traditional security tools finish their assessment, the resource is gone.
Distributed architectures span everywhere. Your critical application might touch 40 different services across three cloud providers and your on-premises data center. An attack that exploits this distributed nature doesn’t fit neatly into any single tool’s domain.
Configuration happens automatically. With infrastructure as code and CI/CD pipelines, your environment changes dozens of times per day. Point-in-time compliance checks become mostly useless—you need continuous monitoring that can keep up with this pace of change.
The attack surface expanded. Each microservice is a potential entry point. Each container image could contain vulnerabilities. Each cloud permission that’s set too broadly creates a pathway for attackers. The number of things you need to protect grew exponentially.
Traditional security built on signature-based detection, manual reviews, and well-defined perimeters simply can’t operate at this speed or scale.
The Problem Your Team Is Actually Experiencing
If you’re managing cloud-native infrastructure, you’ve probably felt some combination of these frustrations:
You don’t have real visibility. You know you have thousands of cloud resources, but nobody can answer basic questions: Which ones are exposed? Which contain sensitive data? Which have excessive permissions? That feeling of blind spots—that’s not just discomfort, it’s genuine risk.
Your alerts are useless. Security teams report receiving thousands of alerts daily. Most are false positives. Some contradict each other (one tool says medium risk, another says critical). The signal-to-noise ratio is so bad that critical threats get missed in the volume.
Security and development live in different worlds. Your developers need to move fast. Your security team needs things to be careful. These teams often feel like they’re fighting each other rather than working together. Issues discovered in production are expensive and stressful to fix.
You’re paying for redundancy. Different tools handle similar functions. You’re licensing multiple platforms that overlap significantly. The total cost is substantial, and the benefit is fragmented.
Compliance reporting is a nightmare. When an auditor asks whether your infrastructure meets PCI or HIPAA standards, the answer involves manually collecting evidence from multiple systems, correlating it, and building a narrative. It’s time-consuming and leaves room for error.
These aren’t minor nuisances. They directly impact your organization’s risk profile and your team’s effectiveness.
The Numbers Don’t Lie
Here’s what keeps security executives up at night: organizations know they have problems, but they can’t fix them fast enough.
Nearly half of surveyed organizations regularly push code with known vulnerabilities to production. Not because they’re reckless, but because fixing vulnerabilities in cloud-native applications often requires coordination across multiple teams, updates to multiple microservices, and careful orchestration to avoid breaking things. It’s easier to accept the risk and plan to fix it “soon.”
97% of organizations experienced a cybersecurity incident related to internally developed applications in the previous year. These aren’t sophisticated nation-state attacks—these are preventable incidents caused by misconfigurations, excessive permissions, unpatched vulnerabilities, and exposed secrets. The kind of stuff security tools should catch, but don’t because of tool sprawl and lack of context.
Breaking Down CNAPP: What You’re Actually Getting
“Cloud-Native Application Protection Platform” is a dense term, so let’s unpack what it actually means: it’s a single platform that handles multiple security functions that used to require separate tools.
These functions address different parts of the problem, but they work together to create something genuinely more useful than the sum of its parts.
Understanding the Core Components
Cloud Security Posture Management (CSPM)
This is the part that continuously looks at your cloud infrastructure and asks: “Is this configured securely?”
It automatically discovers all your cloud resources (databases, storage buckets, virtual machines, network configurations, identity roles, everything). It then evaluates them against security standards and compliance requirements. When it finds something concerning—an unencrypted database, a publicly accessible storage bucket, excessive permissions—it alerts you.
The “posture” part is important: it’s not looking for active attacks; it’s checking that your infrastructure follows security best practices. CSPM is like a hygiene inspector for your cloud environment.
Must Read: CSPM Tools in 2025: Built‑In vs Third‑Party vs Open‑Source (and When to Choose Each)
Cloud Workload Protection Platform (CWPP)
If CSPM is about infrastructure configuration, CWPP is about what’s actually running on that infrastructure.
It protects containers, virtual machines, and serverless functions while they’re executing. It scans container images for vulnerabilities before they’re deployed. It monitors running workloads for suspicious behavior—unexpected network connections, unusual file modifications, attempts to escalate privileges.
CWPP uses behavioral analysis to distinguish between normal activity and potential threats. It’s more sophisticated than checking a list of known vulnerabilities; it looks at what the workload is actually doing.
Cloud Infrastructure Entitlement Management (CIEM)
This addresses one of the most exploited cloud security weaknesses: excessive permissions.
In cloud environments, it’s common to give services or users broader permissions than they actually need. It feels safer—less chance of things failing. But it creates significant risk. If an attacker compromises one of these overprivileged identities, they can potentially access far more than necessary.
CIEM maps out all your cloud identities (both human users and service accounts), analyzes their permissions, and identifies where you’re granting more access than necessary. It helps enforce the principle of least privilege—give everything the minimum permissions it needs to do its job.
Infrastructure as Code (IaC) Security
Infrastructure as code means your cloud infrastructure is defined in files—Terraform templates, CloudFormation scripts, Kubernetes manifests. This creates an opportunity to catch problems before they’re deployed.
IaC security scanning reads these files before they’re applied and looks for misconfigurations, hardcoded secrets, security anti-patterns. Instead of discovering problems after they’re in production (expensive to fix), you find them during development (cheap to fix).
This is “shifting left” in practice—moving security earlier in the process.
Kubernetes Security Posture Management (KSPM)
If your infrastructure includes Kubernetes (and increasingly, many organizations’ do), KSPM handles security specific to that environment.
Kubernetes introduces its own security complexities: role-based access control policies that can be overly permissive, network policies that might not segment traffic properly, workload security settings that could allow privilege escalation. KSPM addresses these Kubernetes-specific concerns.
Cloud Detection and Response (CDR)
This is where everything comes together. CDR correlates security signals across your entire environment—misconfigurations, vulnerable workloads, risky permissions, suspicious behavior—and identifies threats.
More importantly, it provides context. It doesn’t just say “container contains a critical vulnerability”; it says “container with a critical vulnerability is running with root privileges, accessible by a compromised service account, processing customer data.” This context transforms generic alerts into genuinely actionable intelligence.
Also Check: What Is Cloud Detection and Response (CDR)? The Complete 2025 Guide
Data Security Posture Management (DSPM)
Your cloud infrastructure contains data. DSPM focuses on protecting it.
It discovers where sensitive information lives (databases, storage buckets, data lakes). It classifies data based on sensitivity. It monitors who accesses what. It ensures sensitive information is encrypted appropriately. It prevents misconfigured data stores from being publicly accessible.
Data breaches are among the most costly security incidents. DSPM specifically addresses the data layer.
How these Components Actually Work Together
The real power of a unified CNAPP isn’t in any single component—it’s in their integration.
Consider a real scenario: A developer deploys a Kubernetes application. The IaC security scanning caught that the container image had no vulnerabilities—good. KSPM checked that the cluster configuration follows security standards—good. CSPM confirmed cloud resources are configured appropriately—good. But CIEM noticed the service account has permissions to read from three different databases, though the application only needs access to one.
A fragmented toolset might flag the excessive permissions but provide no context about whether it’s actually exploitable or risky. A unified CNAPP correlates these signals and tells you: “The service account has overly broad permissions to databases containing customer PII, and the container is exposed to the network via an API. This is a real risk that should be addressed before going to production.”
The context matters. It transforms noise into signal.
You can Read in Detail: Context-Based Prioritization for CSPM: Fix What Actually Reduces Risk
The Real Business Case for Consolidation
Implementing a unified platform isn’t just about better security. There’s a genuine financial argument too.
The Hidden Cost of Fragmentation
Most organizations don’t calculate the actual cost of managing multiple security tools. It includes the obvious licensing costs, but also:
Operational overhead. Your security team switches between dashboards. They manually correlate alerts from different tools. They manage separate policies, separate integrations, separate training. This isn’t efficient—it’s wasteful.
Alert fatigue causing missed threats. When your teams receive thousands of alerts daily and most are false positives, two things happen: actual critical alerts get missed, and your teams become desensitized to alerts. Both outcomes increase risk.
Slower response to incidents. When information about a threat is scattered across multiple systems, incident response takes longer. Longer response means attackers have more time to cause damage.
Security becoming a bottleneck. If security reviews require manual checks across multiple tools, deployment processes slow down. Development teams get frustrated. Eventually, teams find ways around security processes—which is worse than no security.
Expensive remediation in production. When issues are found after deployment, they’re expensive to fix. They require emergency patching, potentially cause service disruptions, require rollbacks. When issues are caught earlier (through IaC security or during CI/CD integration), they’re dramatically cheaper to address.
Learn More On: How to Use Graph-Driven Visualization for Threat Hunting | Cy5 CSPM Tool
The Actual Financial Impact
Organizations typically see ROI from CNAPP consolidation within 6-12 months through:
Reduced licensing. Most organizations can eliminate 5-8 separate security tool licenses. These savings are immediate and tangible.
Reduced operational cost. Security teams spend less time managing tools and more time on strategic work. This translates to either reduced headcount needs or more value from your existing team.
Faster development cycles. When security integrates seamlessly into CI/CD pipelines rather than creating friction, deployments move faster. This accelerates time-to-market, which has real business value.
Fewer successful attacks. Improved detection, faster response, better context—these reduce the likelihood of successful attacks. A single prevented data breach (average cost: over $4 million according to IBM data) pays for years of CNAPP investment.
Compliance efficiency. Automated compliance monitoring and evidence collection reduces the time and cost of preparing for audits. For organizations under heavy compliance requirements, this alone can justify the investment.
The financial case is there, but it’s often secondary to the security improvement. Better visibility, faster threat detection, and reduced alert fatigue are valuable whether or not you’re tracking them financially.
How CNAPP Actually Works in Practice
Understanding CNAPP theoretically is one thing. Seeing how it actually functions in real scenarios is another.
Kubernetes Deployment Protection
Your development team commits Kubernetes manifests to your repository. These files define how your containerized application will run—which image to use, what permissions to grant, what resources it needs.
With IaC security in place, these manifests get scanned immediately. The system identifies that the Deployment is trying to run as root—a security anti-pattern. It flags that there’s no resource limits defined, which could allow the container to consume excessive resources. It notes that the container image is pulling from a public registry, which introduces supply chain risk.
Your developer gets immediate feedback: “Your manifest has three security issues. Here’s how to fix them.” The fixes are straightforward—switch to running as a non-root user, add resource limits, use an internal container registry.
Once deployed, KSPM continuously monitors the cluster. When you update your RBAC policies or network policies, it validates that these changes follow security practices. When pods are running, CWPP monitors their behavior for anomalies.
Later, an attacker compromises one service through an unrelated vulnerability. That service tries to perform actions it shouldn’t be able to—accessing secrets it doesn’t have permissions for, or connecting to databases outside its normal communication pattern. Both of these behaviors get flagged. CDR correlates these with other signals and alerts your team before significant damage occurs.
The entire workflow—from developer writing code to detecting an actual compromise—is protected by security controls that operate without slowing down development.
Check Out: From Policy to Proof: Automating Evidence for NIST/CIS With CSPM + AI
Multi-Cloud Governance
Your organization uses AWS for compute-heavy workloads, Azure for analytics, and Google Cloud for certain ML applications. Managing security across these environments traditionally meant dealing with each provider’s native tools—AWS Security Hub, Azure Security Center, Google Cloud Security Command Center.
A unified CNAPP presents a single dashboard showing security posture across all three environments. You define security policies once. The platform translates these into environment-specific controls for each cloud provider.
When you need to demonstrate compliance with PCI DSS, you don’t gather evidence from three different tools. Your CNAPP provides a comprehensive report showing which controls are in place across all environments, where gaps exist, and how they’re being addressed.
During an audit, your auditors review a single report that clearly maps your security practices to specific compliance requirements. You spend less time on compliance theater and more time on actual security.
Do Give a Read: Cloud Security Architecture (2025): Frameworks, Layers & Reference Diagram
Development Team Integration
Your development team uses GitHub for version control and GitHub Actions for CI/CD. Traditionally, security happens after code is merged—either in a separate review process or after deployment.
With CNAPP integration, security happens in the development workflow itself. When a developer opens a pull request, automated security checks run:
- IaC security scans any infrastructure definitions
- Dependency scanning checks for known vulnerabilities in libraries
- Container scanning validates the image before it’s deployed
- Policy checks ensure the change complies with your security standards
Issues get flagged in the pull request itself. The developer sees: “Your Terraform template has an issue: this S3 bucket would be publicly accessible. Change the ACL to private.” The fix takes 30 seconds. The PR gets approved. Nobody’s workflow is disrupted.
This is shift-left security in practice. Issues are caught and fixed by the team who understands the code best (the developers) at the point where it’s easiest to fix (before it’s deployed).
Comparing Old Security Methods to Modern Platforms
It’s worth understanding what changes fundamentally when you move from fragmented point solutions to unified CNAPP.
Information Silos vs. Contextual Intelligence
Old approach: CSPM reports misconfiguration. CWPP reports vulnerability. CIEM reports overprivileged access. These are three separate alerts that nobody connects.
New approach: “Container with critical vulnerability (in CWPP) runs with excessive permissions (in CIEM) on a misconfigured cluster (in KSPM). This is exploitable.”
The second approach provides actual intelligence. The first provides information that requires manual correlation.
Manual Triage vs. Intelligent Prioritization
Old approach: Security team receives 5,000 alerts daily. Most are low-priority or false positives. Team manually triages, trying to identify which ones matter. Exhausting. Error-prone.
New approach: 5,000 raw security signals get processed by a system that understands context. The system delivers 50 prioritized findings—things that are actually risky given your environment, your data, and your permissions. Team focuses on things that actually matter.
This reduces alert fatigue dramatically. Security teams consistently report that consolidation reduces alert volume by 60-80% while actually improving detection quality.
Point-in-Time Compliance vs. Continuous Compliance
Old approach: Auditors come annually. Organization scrambles to collect evidence that configurations were correct (or tries to improve configurations quickly). After auditors leave, things drift back to how they were before.
New approach: Compliance is monitored continuously. When infrastructure deviates from compliant configurations, alerts get triggered. Compliance reports are generated automatically using current, accurate data. Audits become validation of continuous compliance rather than point-in-time assessment.
Friction-Heavy Security vs. Frictionless Integration
Old approach: Development team writes code. Security team reviews code. Security finds issues. Development team fixes issues. Code gets deployed. Security was a gate that slowed things down.
New approach: Security checks run automatically during development. Developers see security feedback in real-time. Issues get fixed immediately because the developer is actively working on that code. Security is woven into the process rather than bolted on top.
This might sound like a small difference, but it’s fundamental. When security enables development rather than blocking it, everything changes—developer adoption, response times, even the quality of security practices.
Reactive Incident Response vs. Proactive Threat Prevention
Old approach: Alert comes in about suspicious behavior. Team investigates whether it’s real. By then, attacker has already achieved their objective. Team focuses on damage control and forensics.
New approach: Potential attack paths are identified and remediated before they’re exploited. When suspicious behavior does occur, contextual information shows immediately whether it’s exploitable. Team can respond faster and more precisely.
This shift from reactive to proactive is powerful. It’s the difference between reacting to fires and preventing fires.
Check Out: Secure Cloud Architecture Design: Principles & Patterns; Best Practices
Making the Right Choice: What to Look for in a CNAPP
You’ve decided consolidation makes sense. Now comes the challenging part: actually selecting a platform.
Comprehensiveness Matters
First, verify the vendor actually offers a comprehensive CNAPP. Some platforms market themselves as CNAPP but really only offer CSPM + CWPP. That’s better than separate point solutions, but it’s not complete.
Ask directly: Do you offer all seven components? CSPM, CWPP, CIEM, IaC security, KSPM, CDR, DSPM? If they’re missing pieces, you’ll still need other tools—which defeats some purpose of consolidation.
Multi-Cloud Support Isn’t Optional
Most organizations work with multiple cloud providers. Ask which clouds are supported. AWS and Azure are table stakes. If the vendor only supports one or two providers, that becomes a limiting factor.
Similarly, ask about Kubernetes support. If you’re running Kubernetes and the vendor’s KSPM is weak, you’re still missing critical coverage.
Developer Experience Matters More Than You’d Think
Visit the vendor’s demo environment yourself. Look at how feedback is delivered to developers. Is it clear and actionable? Would your developers actually use it, or would they see it as noise?
Check whether the platform integrates with your CI/CD tools (GitHub, GitLab, etc.). Integration quality varies significantly. A vendor that treats developer workflows as an afterthought will create friction rather than reducing it.
Alert Quality Over Alert Quantity
Ask the vendor about their approach to alert prioritization. Do they apply intelligence to reduce noise? Can you configure alert rules for your specific environment? Do they correlate signals across multiple layers?
Some vendors generate massive alert volumes. Others have genuinely reduced alert volumes while improving detection quality. The difference is significant.
Risk Scoring Should Make Sense
How does the vendor calculate risk? Is it based purely on vulnerability severity (which is limited)? Or does it include context—whether the vulnerability is actually exploitable in your environment, whether the affected resource processes sensitive data, whether an attacker could reach it?
Better risk scoring leads to better prioritization. This matters more than you’d think.
Must Read: How to Use Entity-Driven Analytics for Threat Detection
Automation and Response Capabilities
Can the vendor automate remediation for common issues? If you discover a misconfiguration, can the platform automatically fix it? Or do you still have to manually remediate everything?
What about incident response? If a threat is detected, can the platform automatically take actions (isolate a workload, revoke suspicious permissions)? Or does everything require manual intervention?
Automation reduces the workload on your security team significantly.
Compliance Reporting
If you’re under regulatory requirements, ask specifically about compliance support. Which frameworks are supported? Can you create custom compliance policies for your specific requirements? How is evidence collected and reported?
For organizations dealing with PCI, HIPAA, SOC 2, or other regulations, compliance automation is valuable.
Scalability and Performance
Ask about the platform’s performance in large-scale environments. Can it handle thousands of cloud resources? Hundreds of Kubernetes clusters? What’s the overhead of agents or monitoring?
Performance degradation matters. If implementing the platform slows down your applications or your deployments, you’ve made things worse, not better.
Vendor Stability and Support
This is a security platform. You’re depending on it. Check the vendor’s financial stability. Look at their market position. Ask about customer references.
Also ask about support. For security tools especially, support quality matters. What are response times for issues? Is 24/7 support available? Do they provide professional services to help with implementation?
Implementation Complexity
Ask directly: How long does implementation take? What’s the learning curve for your team? Can the vendor help with onboarding?
Some platforms are more complex than others. If implementation takes six months and requires extensive training, that affects the timeline to value.
Also Read: Security Data Lake vs SIEM: When to Split Ingest and Analytics
Where Cloud Security is Heading
Understanding trends helps you make decisions that don’t look outdated in two years.
More Intelligence, Less Configuration
As AI and machine learning become more sophisticated, security platforms will provide more intelligence and require less manual configuration. Instead of writing rules, you’ll define high-level policies and let the system figure out the details.
Earlier Detection in the Pipeline
Security is steadily moving earlier in the development process. Today, IaC security happens during development. Tomorrow, security analysis might happen during design phases. The earlier issues are found, the cheaper they are to fix.
Better Context and Automation
Current platforms provide good context. Future platforms will understand even more about your business. They’ll know which data is most critical, which services are revenue-generating, and prioritize accordingly. Automation will increase—not just detecting issues but remediating them automatically with appropriate guardrails.
Identity and Access Becoming Central
As cloud complexity increases, identity becomes increasingly critical. Platforms that excel at CIEM (identity entitlement management) and can correlate identity with other security signals will be more valuable.
Integration with Broader Security Ecosystems
CNAPP won’t be standalone. It will integrate deeply with SIEM (Security Information and Event Management), SOAR (Security Orchestration, Automation, and Response), and XDR (Extended Detection and Response) platforms. The future of enterprise security is orchestrated security across multiple domains.
Consolidation Will Continue
Gartner predicts that by 2026, 80% of enterprises will consolidate cloud-native security to three or fewer vendors. This consolidation trend is real and will accelerate. Point solutions for niche problems might survive, but comprehensive platforms will dominate.
Also Read: AI for CSPM: 7 Practical Use‑Cases That Reduce Noise and Prove Compliance
Common Questions Teams Ask
Q: How much do CNAPP platforms cost compared to buying point solutions separately?
Cost varies significantly by platform and by what you’re protecting. Generally, consolidating 5-8 separate tools into one platform reduces licensing costs by 30-50%. Additional savings come from reduced operational overhead. Full ROI typically occurs within 6-12 months.
Q: Can we migrate from our current tools gradually, or does it have to be a big-bang replacement?
Most vendors support gradual migration. You can bring your cloud accounts into the CNAPP platform over time. You can run the new platform in parallel with existing tools initially, then phase out old tools as you gain confidence in the new platform.
Q: What happens to our existing security policies when we move to a new platform?
This is vendor-dependent. Some platforms make it relatively easy to import existing policies and refine them. Others require rebuilding policies in the new system. During evaluation, test how easily policies can be migrated.
Q: How do we handle vendor lock-in concerns?
Fair concern. Ask the vendor about data export capabilities. Can you export your findings, alerts, and configurations? What’s the switching cost if you want to move to a different platform later?
Look for platforms that use standard formats for data export. Some vendors make it easy to leave; others make it difficult. This matters.
Q: What’s the learning curve for our security team?
Depends on the platform. Some are more intuitive than others. Ask for training and documentation. Can the vendor provide initial training for your team? Most quality vendors provide some level of onboarding support.
Q: How does this work with our existing SIEM?
Most modern CNAPP platforms integrate with SIEM tools. They can send security findings into your SIEM, enriching your security events with cloud context. Ask specifically about SIEM integration capabilities.
Q: Will this improve our incident response time?
Yes, typically significantly. Better visibility, contextual alerts, and automated response all reduce MTTR (mean time to respond). Early customers report 30-50% reductions in incident response time.
Must Read: Public Cloud vs Private Cloud (2025): Security, Cost & Compliance Compared
Making Your Move
If you’re currently managing fragmented cloud security tools, consolidation is worth serious consideration. The security improvement alone—better visibility, faster detection, reduced noise—justifies the effort.
The journey typically looks like:
- Assessment phase: Understand your current security posture, identify gaps, and clarify requirements. What compliance frameworks apply to you? What cloud environments do you need to protect? What workload types do you use?
- Evaluation phase: Research and demo 2-3 platforms that meet your requirements. Involve your team in the evaluation. The platform needs to work for them, not just for leadership.
- Pilot phase: Implement the platform in a limited scope first. Connect a few cloud accounts or clusters. Run it in parallel with existing tools while building confidence.
- Expansion phase: As comfort grows, expand coverage. Bring additional cloud accounts into the platform. Retire old tools as they become redundant.
- Optimization phase: Refine policies, integrate with other security tools, automate remediation workflows, and optimize for your specific needs.
The entire process typically takes 3-6 months from initial consideration to full deployment.
What’s Next?
The shift toward unified cloud-native security isn’t about technology for its own sake. It’s about addressing real weaknesses in how organizations protect their cloud infrastructure. Fragmented tools create blind spots, alert fatigue creates missed threats, and friction in the security process creates workarounds that undermine security.
A unified CNAPP platform addresses these structural weaknesses.
If you’re responsible for cloud security and you’re managing multiple point solutions, it’s worth exploring whether consolidation makes sense for your organization. The business case—better security, faster response, reduced operational cost, improved compliance—is compelling.
The specific platform that’s right for you depends on your requirements, your environment, and your team. But the value of moving away from fragmentation toward unified cloud-native protection is increasingly difficult to argue against.
Ready to Explore Unified Cloud Security?
See How Cy5 Approaches Cloud-Native Protection
Get a Custom Assessment of Your Current Security
Learn More About Cloud-Native Security





