Welcome to Part 1 of a blog series that would cover various AWS services, and documented in a manner that a seasoned security or cloud practitioner could easily relate to. The idea here is not to deep dive into specific services, but to be a ready reckoner for security and devops teams embarking on a “security at scale” journey. Part 1 covers AWS networking services that deal with Perimeter or Network Security.
The perimeter is the first line of defence in an enterprise!
Just like hosted data centres, network is a crucial piece of the security landscape. However, bear in mind that unlike hosted data centres where every component was “within” a tight perimeter secured by firewalls, public cloud environments consist of a combination of services that are accessible to the internet as well. These include services, such as S3, API gateways. This is an excellent video outlining how perimeters are different in public cloud environments.
Without further ado, let’s deep dive into certain AWS networking services that benefit network and security teams alike.
AWS Shield
The AWS service helps customers defend against network attacks such as denial of service or distributed denial of service. DoS / DDoS attacks have been around for a while and used as mean to disrupt a victim organisation’s operations. Imagine you were an e-Commerce setup who’s primary business is generated from customers purchasing products from your website. A denial of service attack would have a direct impact to business since it would inhibit genuine customers from making purchases from the website.
There are two options AWS provides when it comes to it’s Shield service:
- Shield Standard helps detect and prevent layer 3 & layer 4 denial of service attacks against your AWS infrastructure.
- Shield Advanced on the other hand, provides comprehensive protection towards multiple AWS services such as Application Load Balancers, EC2, CloudFront. In addition to this, customers also benefit from access to a dedicated 24×7 incident response team (AWS Shield Response Team), among other benefits detailed here.
Depending upon the scale of operations and requirements, customers can opt for the AWS Shield Advanced over it’s Standard version.
AWS Web Application Firewall
Web applications account for a larger part of the internet, and so do it’s attacks and threat vectors. The OWASP Top 10 list gives a clear and crisp insight into these attack types. A web application firewall helps defend against some of these typical attack types and are widely used for applications that are internet facing.
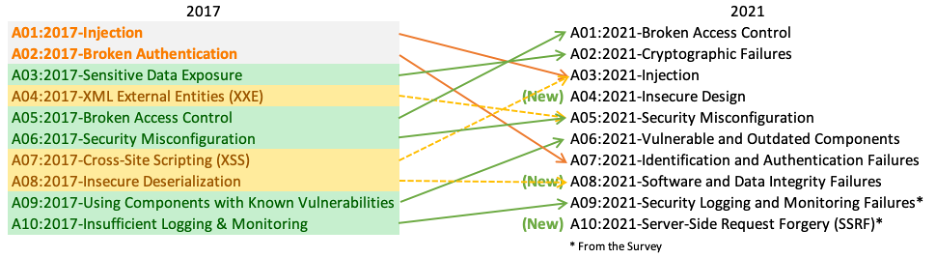
Source: OWASP Top 10
The AWS WAF is a managed web application firewall service that enables AWS customers to quickly enable layer 7 protection on their applications. It integrates seamlessly with AWS services such as CloudFront, Application Load Balancers, API Gateway to protect applications.
Types of protection
The AWS WAF is shipped with a bunch of managed rule-sets that could be applied for a variety of use cases. These include:
- Baseline rule groups – these are rules most commonly used for the well known attack types as well as ensure that the incoming HTTP requests are in line with the HTTP protocol specifications
- Use case specific rule groups – address specific attack types that are targeted towards a particular kind of environment, such as Windows, Linux, SQL databases.
- IP reputation rule groups – comprise a list of IP addresses that are known to possess a negative reputation. These could be compromised servers, TOR exit nodes or known botnets.
- Bot control rule groups – are targeted towards scrapers or automated tools that crawl websites in an unauthorised manner.
- Account takeover rule groups – protect web application login forms from credential stuffing attacks.
Network Reachability
Cloud network deployments are complex and extremely dynamic, and hence it becomes important to keep a watch when resources are inadvertently opened up beyond permitted boundaries. Inspector’s network reachability component does exactly this. The reachability analyzer scans configurations of various AWS resources such as EC2 instances, load balancers, direct connect, network interfaces to establish where they are reachable from.
The results from a network reachability component call out reachability routes, ie. whether a resource is accessible from the internet, a peered VPC or a virtual private gateway. In case the results seem interesting (or suspicious), these can be further analysed by the VPC Reachability Analyser utility. Given a source and a destination, the utility generates a precise network access path, which is immediately able to pin-point the area of concern. For example, in case there is a database accessible from the internet, the utility can point out the exact security group causing the exposure.

Source: AWS
Firewall Manager
Any production AWS deployment is loaded with EC2 instances, ALBs which have various security groups and NACLs associated with them. Added to that, public applications would require Web Application Firewalls, which would in turn require management of rules. Maintaining these configurations at an individual level can become a nightmare and can be catastrophic if mis-configured.
The AWS Firewall Manager eases out management of security groups, WAF rules and Shield configurations of your AWS environment by providing a single pane of glass to configure, deploy and manage them across multiple AWS accounts and workload.
Apart from management, the AWS Firewall Manager can also be used to enforce organizational policies consistently across a cloud deployment, for example, ensuring port 22 or 3389 (ie. SSH or Remote Desktop) is never opened up from 0.0.0.0/0 (ie. the internet).
NAT Gateway
Though not directly a security related service, the NAT gateway plays an important role in managing network traffic that leaves a VPC, and this is how:
- Hides IP address of internal systems when they talk to the internet
- Does not require workload to have individual public IP addresses for internet bound communication
- Enables a zoned network architecture, such that workload in a private network are able to communicate with the internet
VPC Flow Logs
Logging is an integral part of a security implementation, and VPC flow logs are crucial to gain visibility into network activity that occurs within an VPC. Flow logs can be enabled on any workload network interface or AWS network services such as NAT gateways, Transit gateways etc. Below are the key fields that appear as a part of a flow log:
- AWS Account
- Network Interface
- Source IP
- Source Port
- Destination IP
- Destination Port
- Action (Allow / Deny)
Here’s what a VPC flow log looks like:
2 123456789010 eni-1235b8ca123456789 172.31.16.139 172.31.16.21 20641 22 6 20 4249 1418530010 1418530070 ACCEPT OK
Further, these logs can be sent to CloudWatch for easing out analysis and investigations. Check out the article here that describes the integration approach.
Site-to-Site VPN and VPC Peering
Workload that’s deployed in a VPC can communicate with other resources within the same VPC. However, in order to establish connectivity with other VPCs as well as customer premises or hosted data centers, customers require additional network configurations.
Site-to-Site VPN connections enable customers to connect their premises or hosted data centers to an AWS VPC whereas VPC peering is leveraged to establish connectivity with one or more VPCs. This is extremely useful while connecting multiple networks together, and when done right from the very beginning, goes a long way in maintaining a clean and manageable network.
Conclusion
Our next post would cover AWS services that revolve around other security verticals such as Data Security, Infrastructure Security etc.