Well it’s not unheard of, that security issues, malware or exploits often follow soon after an emerging technology finds prominence.
Denonia, the first Lambda malware is out.
Originally discovered by Cado Labs a few days ago, Denonia specifically targets Lambda functions with the intent to deploy code that carries out bitcoin mining, hence significantly increasing AWS costs for the impacted organisation.
Let’s break this down a little now.
What is Lambda?
Lambda (or Lambda Functions) is an AWS service that helps it’s customers run applications without using servers. Such a deployment or mechanism of running applications is also called serverless. Organisations can choose from a variety of platforms such as Python, Go, NodeJS to develop their applications and then deploy them on Lambda.
There are various reasons Lambda Functions are considered a tad more secure than traditional VM based or hardware based deployments, here are some:
Reduced Attack Surface
Fine Grained Permissions
Reduced Execution Time
What is Denonia anyway?
Technical Details
Preventing Denonia
Denonia runs on Lambda, and an attacker requires elevated access to deploy the malware as a Lambda function.
Limit Access Keys
- Avoid storing these in code.
- Avoid creating multiple access keys unless absolutely necessary.
- Use short lived credentials instead.
Fine Grained Permissions
- Grant permissive access to IAM roles or users in a restrictive manner.
- Avoid using “FullAccess” policies.
- Use fine grained IAM policies where possible, restricting access to Actions as well as Resources
Detecting Denonia
It is always a good idea to complement preventive security controls, with ones that can detect compromise or unusual activity.
Let’s see how detective controls can work towards catching Denonia.
For this malware, we are going to analyse VPC flow logs assuming the Lambda function is configured in a VPC and the VPC has flow logs enabled.
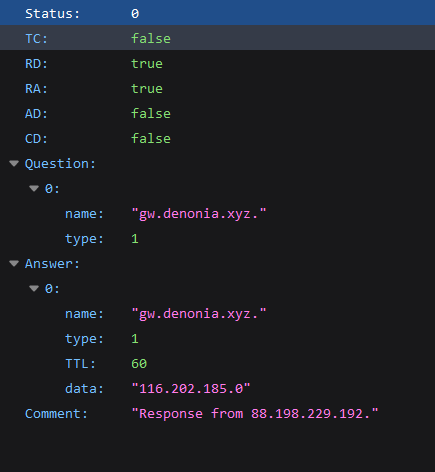
After the malware has resolved the gw[.]denonia[.]xyz domain to it’s corresponding ip address and written it in the /tmp directory, it sends a request at port 3333 (XMRig mining pool) of the same IP address which gets logged in VPC Flow logs.
Hence, any request to port 3333 should be a red flag – this is a port that’s not very commonly used.
A sample VPC flow log for such a communication is as below.
2 123456789010 eni-1235b8ca123456789 172.31.16.139 116[.]203[.]4[.]0 20641 3333 6 20 4249 1418530010 1418530070 ACCEPT OK
Beyond Standard Detection
We looked at some very simple means of detecting Denonia. However, attackers are smart and would evolve to fly under the radar by establishing connections over benign ports such as 443 or 80, which are commonly used for HTTP traffic. This makes the job harder for security analysts to catch malicious communication.
Well, it’s not all bad news.
Detection techniques have also evolved with next generation threat detection systems. Such systems can now flag unusual activity based on past trends and traffic patterns.
For example, in case of Denonia, one could look for the below behavior:
- Excessive outbound connections to multiple geo locations
- Unusual number of outbound connections
- Increase in traffic volume
- Anomalous increase in AWS Lambda cost (via AWS billing alarms)
Cy5 ion to Detect & Prevent Denonia
ion – Cy5’s flagship cloud security product ships with 200+ security configuration checks and threat detection use cases. Let’s look at how some of these can help prevent or catch Denonia early on in it’s game.
Via Cloud Security Checks
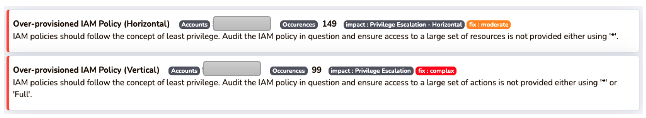
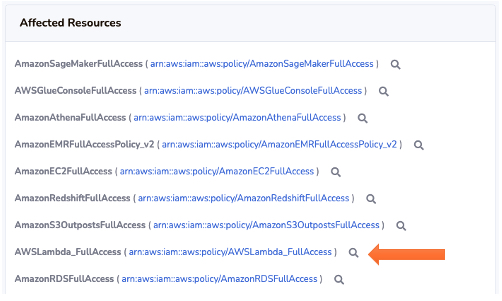
Here are some configuration checks that can alert on overly provisioned IAM policies or excessive access keys usage.
Via Threat Detection
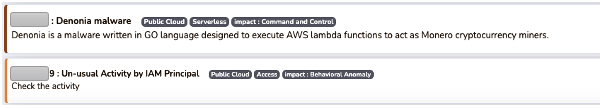
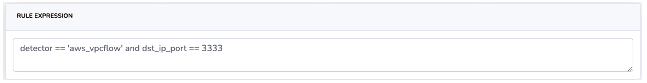
Here is a sample rule to catch outbound communication on port 3333:
Conclusion
Though Denonia is a new malware and a first that targets AWS Lambda, it’s deployment and execution tactic exploits weaknesses that have been known and around for a while. Implementing IAM best practices and leveraging detection technology that can catch standard and advanced threats is key to preventing such malware from making way into a public cloud ecosystem.
We hope this post was helpful, stay updated with the latest in cloud security by subscribing to our newsletter.



